編輯:關於Android編程
CF1、驅動的簡單測試
在上一篇文章中,我們已經把添加驅動模塊做完了,並把驅動下載到了板子上。下面將介紹一下如何測試驅動是否正常。
這個ttt驅動,我們實現了一個讀、一個寫的接口,就此進行簡單的測試:
啟動板子,進入系統,然後進入命令行(可以用串口,也可以用adb shell)
進入dev目錄:
這裡就可以說明: ttt 設備文件已經OK了,輸入輸出接口都沒有問題。
當然,這裡還有其他的方式去驗證這個輸入輸出,如:
進入到 /sys/class 的 ttt 設備目錄下:
power
subsystem
uevent
power
subsystem
uevent
val
2、編寫C程序來測試驅動的讀寫
切換到root權限,並進入到android源碼目錄下的 external 目錄:
antlr fsck_msdos libvpx skia
apache-harmony genext2fs libxml2 sonivox
apache-http giflib libxslt speex
apache-xml google-diff-match-patch libyuv sqlite
astl grub llvm srec
bison gtest lohit-fonts srtp
blktrace guava markdown stlport
bluetooth harfbuzz mesa3d strace
bouncycastle hyphenation mksh svox
bsdiff icu4c mockwebserver tagsoup
bzip2 iproute2 mtpd tcpdump
chromium ipsec-tools netcat tinyalsa
clang iptables netperf tinyxml
collada javasqlite neven tremolo
dbus javassist nist-sip v8
dhcpcd jdiff oauth valgrind
dnsmasq jhead opencv webkit
doclava jpeg openssl webp
dropbear jsilver oprofile webrtc
e2fsprogs jsr305 pcre wpa_supplicant
easymock junit ping wpa_supplicant_6
elfutils kernel-headers ping6 wpa_supplicant_8
embunit libffi ppp xmlwriter
emma libgsm proguard yaffs2
esd liblzf protobuf yapp
expat libnfc-nxp qemu zlib
eyes-free libnl-headers qemu-pc-bios
fdlibm libpcap quake
flac libphonenumber replicaisland
android-mock freetype libpng safe-iop
antlr fsck_msdos libvpx skia
apache-harmony genext2fs libxml2 sonivox
apache-http giflib libxslt speex
apache-xml google-diff-match-patch libyuv sqlite
astl grub llvm srec
bison gtest lohit-fonts srtp
blktrace guava markdown stlport
bluetooth harfbuzz mesa3d strace
bouncycastle hyphenation mksh svox
bsdiff icu4c mockwebserver tagsoup
bzip2 iproute2 mtpd tcpdump
chromium ipsec-tools netcat tinyalsa
clang iptables netperf tinyxml
collada javasqlite neven tremolo
dbus javassist nist-sip v8
dhcpcd jdiff oauth valgrind
dnsmasq jhead opencv webkit
doclava jpeg openssl webp
dropbear jsilver oprofile webrtc
e2fsprogs jsr305 pcre wpa_supplicant
easymock junit ping wpa_supplicant_6
elfutils kernel-headers ping6 wpa_supplicant_8
embunit libffi ppp xmlwriter
emma libgsm proguard yaffs2
esd liblzf protobuf yapp
expat libnfc-nxp qemu zlib
eyes-free libnl-headers qemu-pc-bios
fdlibm libpcap quake
flac libphonenumber replicaisland
[cpp]
#include <stdio.h>
#include <stdlib.h>
#include <fcntl.h>
#define DEVICE_NAME "/dev/ttt"
int main(int argc, char** argv)
{
int fd = -1;
int val = 0;
fd = open(DEVICE_NAME, O_RDWR);
if(fd == -1){
printf("Failed to open device %s.\n", DEVICE_NAME);
return -1;
}
printf("Read original value:\n");
read(fd, &val, sizeof(val));
printf("%d.\n\n", val);
val = 100;
printf("Write value %d to %s.\n\n", val, DEVICE_NAME);
write(fd, &val, sizeof(val));
printf("Read the value again:\n");
read(fd, &val, sizeof(val));
printf("%d.\n\n", val);
close(fd);
return 0;
}
#include <stdio.h>
#include <stdlib.h>
#include <fcntl.h>
#define DEVICE_NAME "/dev/ttt"
int main(int argc, char** argv)
{
int fd = -1;
int val = 0;
fd = open(DEVICE_NAME, O_RDWR);
if(fd == -1){
printf("Failed to open device %s.\n", DEVICE_NAME);
return -1;
}
printf("Read original value:\n");
read(fd, &val, sizeof(val));
printf("%d.\n\n", val);
val = 100;
printf("Write value %d to %s.\n\n", val, DEVICE_NAME);
write(fd, &val, sizeof(val));
printf("Read the value again:\n");
read(fd, &val, sizeof(val));
printf("%d.\n\n", val);
close(fd);
return 0;
}
創建對應的Android.mk配置文件:
[plain]
root@brantyou-ubuntu:~/workspace/android-4.0.4_r1.2/external/yapp/tttapp# gedit Android.mk
root@brantyou-ubuntu:~/workspace/android-4.0.4_r1.2/external/yapp/tttapp# gedit Android.mk
Android.mk 文件內容如下:
[cpp] view plaincopyprint?LOCAL_PATH := $(call my-dir)
include $(CLEAR_VARS)
LOCAL_MODULE_TAGS := optional
LOCAL_MODULE := tttapp
LOCAL_SRC_FILES := tttapp.c
include $(BUILD_EXECUTABLE)
LOCAL_PATH := $(call my-dir)
include $(CLEAR_VARS)
LOCAL_MODULE_TAGS := optional
LOCAL_MODULE := tttapp
LOCAL_SRC_FILES := tttapp.c
include $(BUILD_EXECUTABLE)
C程序編寫完了,下面進行編譯:
回到android的源碼目錄,並執行envsetup.sh:
[plain]
root@brantyou-ubuntu:~/workspace/android-4.0.4_r1.2# ls
abi build device hardware out system
bionic cts docs libcore packages v8.log
bootable dalvik external Makefile prebuilt vendor
boot.img development frameworks ndk sdk
root@brantyou-ubuntu:~/workspace/android-4.0.4_r1.2# . build/envsetup.sh
including device/moto/stingray/vendorsetup.sh
including device/moto/wingray/vendorsetup.sh
including device/samsung/crespo4g/vendorsetup.sh
including device/samsung/crespo/vendorsetup.sh
including device/samsung/maguro/vendorsetup.sh
including device/samsung/smdkc110/vendorsetup.sh
including device/samsung/smdkv210/vendorsetup.sh
including device/samsung/torospr/vendorsetup.sh
including device/samsung/toro/vendorsetup.sh
including device/samsung/tuna/vendorsetup.sh
including device/ti/panda/vendorsetup.sh
including sdk/bash_completion/adb.bash
including device/moto/stingray/vendorsetup.sh
including device/moto/wingray/vendorsetup.sh
including device/samsung/crespo4g/vendorsetup.sh
including device/samsung/crespo/vendorsetup.sh
including device/samsung/maguro/vendorsetup.sh
including device/samsung/smdkc110/vendorsetup.sh
including device/samsung/smdkv210/vendorsetup.sh
including device/samsung/torospr/vendorsetup.sh
including device/samsung/toro/vendorsetup.sh
including device/samsung/tuna/vendorsetup.sh
including device/ti/panda/vendorsetup.sh
including sdk/bash_completion/adb.bash============================================
PLATFORM_VERSION_CODENAME=REL
PLATFORM_VERSION=4.0.4
TARGET_PRODUCT=full
TARGET_BUILD_VARIANT=eng
TARGET_BUILD_TYPE=release
TARGET_BUILD_APPS=
TARGET_ARCH=arm
TARGET_ARCH_VARIANT=armv7-a
HOST_ARCH=x86
HOST_OS=linux
HOST_BUILD_TYPE=release
BUILD_ID=IMM76I
============================================
target thumb C: tttapp <= external/yapp/tttapp/tttapp.c
target Executable: tttapp (out/target/product/generic/obj/EXECUTABLES/tttapp_intermediates/LINKED/tttapp)
target Symbolic: tttapp (out/target/product/generic/symbols/system/bin/tttapp)
target Strip: tttapp (out/target/product/generic/obj/EXECUTABLES/tttapp_intermediates/tttapp)
Install: out/target/product/generic/system/bin/tttapp
============================================
PLATFORM_VERSION_CODENAME=REL
PLATFORM_VERSION=4.0.4
TARGET_PRODUCT=full
TARGET_BUILD_VARIANT=eng
TARGET_BUILD_TYPE=release
TARGET_BUILD_APPS=
TARGET_ARCH=arm
TARGET_ARCH_VARIANT=armv7-a
HOST_ARCH=x86
HOST_OS=linux
HOST_BUILD_TYPE=release
BUILD_ID=IMM76I
============================================
target thumb C: tttapp <= external/yapp/tttapp/tttapp.c
target Executable: tttapp (out/target/product/generic/obj/EXECUTABLES/tttapp_intermediates/LINKED/tttapp)
target Symbolic: tttapp (out/target/product/generic/symbols/system/bin/tttapp)
target Strip: tttapp (out/target/product/generic/obj/EXECUTABLES/tttapp_intermediates/tttapp)
Install: out/target/product/generic/system/bin/tttapp
root@brantyou-ubuntu:~/workspace/android-4.0.4_r1.2#
這樣就表示編譯成功了,我們看一下這個對應的執行程序是否已經生成:
[plain]
root@brantyou-ubuntu:~/workspace/android-4.0.4_r1.2# ls -l out/target/product/generic/system/bin/tttapp
-rwxr-xr-x 1 root root 5524 2013-04-02 11:04 out/target/product/generic/system/bin/tttapp
root@brantyou-ubuntu:~/workspace/android-4.0.4_r1.2#
root@brantyou-ubuntu:~/workspace/android-4.0.4_r1.2# ls -l out/target/product/generic/system/bin/tttapp
-rwxr-xr-x 1 root root 5524 2013-04-02 11:04 out/target/product/generic/system/bin/tttapp
root@brantyou-ubuntu:~/workspace/android-4.0.4_r1.2# 這樣就表示生成了對應的 可執行程序。
好,現在我們把這個生成的 tttapp 程序拷貝到 SD卡上,然後放到板子上去執行。
我這裡是放到了U盤上面,從U盤中把tttapp 拷貝到板子上的/data目錄中去:
[plain]
root@android:/mnt # ls usb
D3GOther.exe
EBOOT.bin
EBOOT.nb0
IRDA_X.exe
LOST.DIR
MapTools.exe
NK.BIN
NK_2G.bin
NK_3G.bin
NK_3G_y.BIN
NK_src.bin
RFIDForProduce.exe
RFIDTest.exe
RFID_X.exe
STEPLDR.bin
STEPLDR.nb0
SwitchTools.exe
WINCE 6软件
android-samsung-dev_20110830.tar.gz
barscan.exe
bbk
hello
htcbjwdm.inf
tttapp
ubuntu-11.10-desktop-i386.iso
凯立德地图
机身å·ç (MC60端).exe
root@android:/mnt #
root@android:/mnt # ls
asec
ext_sd
obb
sdcard
secure
usb
root@android:/mnt # cd usb/
root@android:/mnt/usb # ls
D3GOther.exe
EBOOT.bin
EBOOT.nb0
IRDA_X.exe
LOST.DIR
MapTools.exe
NK.BIN
NK_2G.bin
NK_3G.bin
NK_3G_y.BIN
NK_src.bin
RFIDForProduce.exe
RFIDTest.exe
RFID_X.exe
STEPLDR.bin
STEPLDR.nb0
SwitchTools.exe
WINCE 6软件
android-samsung-dev_20110830.tar.gz
barscan.exe
bbk
hello
htcbjwdm.inf
tttapp
ubuntu-11.10-desktop-i386.iso
凯立德地图
æ [ttt]: ttt_read().
[ttt]: ttt_write().
[ttt]: ttt_read().
[ttt]: ttt_release().
Read original value:
123.
Write value 100 to /dev/ttt.
Read the value again:
100.
D3GOther.exe
EBOOT.bin
EBOOT.nb0
IRDA_X.exe
LOST.DIR
MapTools.exe
NK.BIN
NK_2G.bin
NK_3G.bin
NK_3G_y.BIN
NK_src.bin
RFIDForProduce.exe
RFIDTest.exe
RFID_X.exe
STEPLDR.bin
STEPLDR.nb0
SwitchTools.exe
WINCE 6软件
android-samsung-dev_20110830.tar.gz
barscan.exe
bbk
hello
htcbjwdm.inf
tttapp
ubuntu-11.10-desktop-i386.iso
凯立德地图
D3GOther.exe
EBOOT.bin
EBOOT.nb0
IRDA_X.exe
LOST.DIR
MapTools.exe
NK.BIN
NK_2G.bin
NK_3G.bin
NK_3G_y.BIN
NK_src.bin
RFIDForProduce.exe
RFIDTest.exe
RFID_X.exe
STEPLDR.bin
STEPLDR.nb0
SwitchTools.exe
WINCE 6软件
android-samsung-dev_20110830.tar.gz
barscan.exe
bbk
hello
htcbjwdm.inf
tttapp
[ttt]: ttt_open().
[ttt]: ttt_read().
[ttt]: ttt_write().
[ttt]: ttt_read().
[ttt]: ttt_release().
Read original value:
123.
Write value 100 to /dev/ttt.
Read the value again:
100.
拷貝的過程中,出現了一些情況,cp指令不可用,使用cat指令就OK了。由上面最後的幾句信息,可以看出這個C程序成功了。測試驅動OK了。
到此,驅動的測試就完了。下一篇將會介紹編寫對應的HAL硬件抽象層來訪問內核驅動
 Android圖片緩存原理、特性對比
Android圖片緩存原理、特性對比
這是我在 MDCC 上分享的內容(略微改動),也是源碼解析第一期發布時介紹的源碼解析後續會慢慢做的事。從總體設計和原理上對幾個圖片緩存進行對比,沒用到他們的朋友也可以了解
 Android 解決build path errors的問題
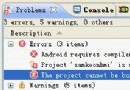
Android 解決build path errors的問題
新建一個eclipse-android項目後,如test2,從其它項目中拷貝若干個包到test2中,在編譯時總會出現以下錯誤:?主要看第三條:The projec
 Android利用Intent實現記事本功能(NotePad)
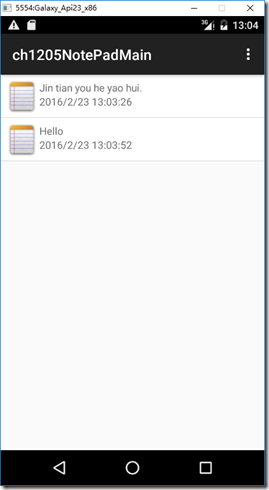
Android利用Intent實現記事本功能(NotePad)
本文實例為大家分享了Intent如何實現一個簡單的記事本功能的演示過程,供大家參考,具體內容如下1、運行截圖單擊右上角【…】會彈出【添加】菜單項,長按某條記錄會彈出快捷菜
 魅藍metal能刷安卓嗎 魅藍metal刷基於安卓Android的flyme OS教程
魅藍metal能刷安卓嗎 魅藍metal刷基於安卓Android的flyme OS教程
魅族這次推出的魅藍metal是基於yunos版本的flymeOS,一些喜歡搞機的用戶當然希望能用回基於Android的flyme,那麼小編來給出一些消息和刷