編輯:關於Android編程
.class public Lcom/qunar/hotel/NextActivity; .super Landroid/support/v7/app/AppCompatActivity; .source "NextActivity.java" # instance fields .field private mLogin:Landroid/widget/Button; .field private mPassword:Landroid/widget/EditText; .field private mUser:Landroid/widget/EditText; # direct methods .method public constructorNextActivity#1.smail文件:()V .locals 0 ... ... return-object v0 .end method # virtual methods .method protected onCreate(Landroid/os/Bundle;)V .locals 2 .param p1, "aSavedInstanceState" # Landroid/os/Bundle; .prologue .line 23 invoke-super {p0, p1}, Landroid/support/v7/app/AppCompatActivity;->onCreate(Landroid/os/Bundle;)V .line 24 sget v0, Lcom/qunar/hotel/R$layout;->activity_next:I invoke-virtual {p0, v0}, Lcom/qunar/hotel/NextActivity;->setContentView(I)V .line 26 sget v0, Lcom/qunar/hotel/R$id;->user:I invoke-virtual {p0, v0}, Lcom/qunar/hotel/NextActivity;->findViewById(I)Landroid/view/View; move-result-object v0 check-cast v0, Landroid/widget/EditText; iput-object v0, p0, Lcom/qunar/hotel/NextActivity;->mUser:Landroid/widget/EditText; .line 27 sget v0, Lcom/qunar/hotel/R$id;->password:I invoke-virtual {p0, v0}, Lcom/qunar/hotel/NextActivity;->findViewById(I)Landroid/view/View; move-result-object v0 check-cast v0, Landroid/widget/EditText; iput-object v0, p0, Lcom/qunar/hotel/NextActivity;->mPassword:Landroid/widget/EditText; .line 28 sget v0, Lcom/qunar/hotel/R$id;->login:I invoke-virtual {p0, v0}, Lcom/qunar/hotel/NextActivity;->findViewById(I)Landroid/view/View; move-result-object v0 check-cast v0, Landroid/widget/Button; iput-object v0, p0, Lcom/qunar/hotel/NextActivity;->mLogin:Landroid/widget/Button; .line 30 iget-object v0, p0, Lcom/qunar/hotel/NextActivity;->mLogin:Landroid/widget/Button; new-instance v1, Lcom/qunar/hotel/NextActivity$1; invoke-direct {v1, p0}, Lcom/qunar/hotel/NextActivity$1;-> (Lcom/qunar/hotel/NextActivity;)V invoke-virtual {v0, v1}, Landroid/widget/Button;->setOnClickListener(Landroid/view/View$OnClickListener;)V .line 40 return-void .end method
.class Lcom/qunar/hotel/NextActivity$1;
.super Ljava/lang/Object;
.source "NextActivity.java"
# interfaces
.implements Landroid/view/View$OnClickListener;
# annotations
.annotation system Ldalvik/annotation/EnclosingMethod;
value = Lcom/qunar/hotel/NextActivity;->onCreate(Landroid/os/Bundle;)V
.end annotation
.annotation system Ldalvik/annotation/InnerClass;
accessFlags = 0x0
name = null
.end annotation
# instance fields
.field final synthetic this$0:Lcom/qunar/hotel/NextActivity;
# direct methods
.method constructor (Lcom/qunar/hotel/NextActivity;)V
.locals 0
.param p1, "this$0" # Lcom/qunar/hotel/NextActivity;
.prologue
.line 30
iput-object p1, p0, Lcom/qunar/hotel/NextActivity$1;->this$0:Lcom/qunar/hotel/NextActivity;
invoke-direct {p0}, Ljava/lang/Object;->()V
return-void
.end method
# virtual methods
.method public onClick(Landroid/view/View;)V
.locals 4
.param p1, "aView" # Landroid/view/View;
.prologue
const/4 v3, 0x0
//判斷用戶名和密碼的正確性
.line 33
iget-object v0, p0, Lcom/qunar/hotel/NextActivity$1;->this$0:Lcom/qunar/hotel/NextActivity;
# getter for: Lcom/qunar/hotel/NextActivity;->mUser:Landroid/widget/EditText;
invoke-static {v0}, Lcom/qunar/hotel/NextActivity;->access$000(Lcom/qunar/hotel/NextActivity;)Landroid/widget/EditText;
move-result-object v0
invoke-virtual {v0}, Landroid/widget/EditText;->getText()Landroid/text/Editable;
move-result-object v0
invoke-virtual {v0}, Ljava/lang/Object;->toString()Ljava/lang/String;
move-result-object v0
const-string v1, "user"
invoke-virtual {v0, v1}, Ljava/lang/String;->equals(Ljava/lang/Object;)Z
move-result v0
//如果equals方法返回true
if-eqz v0, :cond_0
iget-object v0, p0, Lcom/qunar/hotel/NextActivity$1;->this$0:Lcom/qunar/hotel/NextActivity;
# getter for: Lcom/qunar/hotel/NextActivity;->mPassword:Landroid/widget/EditText;
invoke-static {v0}, Lcom/qunar/hotel/NextActivity;->access$100(Lcom/qunar/hotel/NextActivity;)Landroid/widget/EditText;
move-result-object v0
invoke-virtual {v0}, Landroid/widget/EditText;->getText()Landroid/text/Editable;
move-result-object v0
invoke-virtual {v0}, Ljava/lang/Object;->toString()Ljava/lang/String;
move-result-object v0
const-string v1, "123456"
invoke-virtual {v0, v1}, Ljava/lang/String;->equals(Ljava/lang/Object;)Z
move-result v0
//如果equals方法返回true
if-eqz v0, :cond_0
//登錄成功彈出Login Scuess Tost提示
.line 34
iget-object v0, p0, Lcom/qunar/hotel/NextActivity$1;->this$0:Lcom/qunar/hotel/NextActivity;
invoke-virtual {v0}, Lcom/qunar/hotel/NextActivity;->getApplication()Landroid/app/Application;
move-result-object v0
iget-object v1, p0, Lcom/qunar/hotel/NextActivity$1;->this$0:Lcom/qunar/hotel/NextActivity;
invoke-virtual {v1}, Lcom/qunar/hotel/NextActivity;->getResources()Landroid/content/res/Resources;
move-result-object v1
sget v2, Lcom/qunar/hotel/R$string;->login_success:I
invoke-virtual {v1, v2}, Landroid/content/res/Resources;->getString(I)Ljava/lang/String;
move-result-object v1
invoke-static {v0, v1, v3}, Landroid/widget/Toast;->makeText(Landroid/content/Context;Ljava/lang/CharSequence;I)Landroid/widget/Toast;
move-result-object v0
invoke-virtual {v0}, Landroid/widget/Toast;->show()V
.line 38
:goto_0
return-void
//登錄失敗彈出Login Faild Tost提示
.line 36
:cond_0
iget-object v0, p0, Lcom/qunar/hotel/NextActivity$1;->this$0:Lcom/qunar/hotel/NextActivity;
invoke-virtual {v0}, Lcom/qunar/hotel/NextActivity;->getApplication()Landroid/app/Application;
move-result-object v0
iget-object v1, p0, Lcom/qunar/hotel/NextActivity$1;->this$0:Lcom/qunar/hotel/NextActivity;
invoke-virtual {v1}, Lcom/qunar/hotel/NextActivity;->getResources()Landroid/content/res/Resources;
move-result-object v1
sget v2, Lcom/qunar/hotel/R$string;->login_faild:I
invoke-virtual {v1, v2}, Landroid/content/res/Resources;->getString(I)Ljava/lang/String;
move-result-object v1
invoke-static {v0, v1, v3}, Landroid/widget/Toast;->makeText(Landroid/content/Context;Ljava/lang/CharSequence;I)Landroid/widget/Toast;
move-result-object v0
invoke-virtual {v0}, Landroid/widget/Toast;->show()V
goto :goto_0
.end method
4.分析相關Smail和Java文件,通過相關login_success,Toast,equals等關鍵字,閱讀出基本的代碼邏輯。該案例在Java源碼中已經清晰得出用戶名和密碼為user,123456,這裡我們演示如何通過分析修改smail文件“破譯”。閱讀關鍵代碼如下,我們可以將if(mUser.getText().toString().equals("user"))語句修改為if("user".equals("user")),同理if("12345".equals("123456")),即invoke-virtual {v0, v1}修改為invoke-virtual {v1, v1}即可“繞過”用戶名和密碼驗證。實際開發情況會比較復雜,這裡我們僅僅簡單修改用於演示分析過程;
//mUser.getText()
invoke-virtual {v0}, Landroid/widget/EditText;->getText()Landroid/text/Editable;
move-result-object v0
//mUser.getText().toString()
invoke-virtual {v0}, Ljava/lang/Object;->toString()Ljava/lang/String;
move-result-object v0
const-string v1, "user"
//if(mUser.getText().toString.equals("user"))
invoke-virtual {v0, v1}, Ljava/lang/String;->equals(Ljava/lang/Object;)Z
move-result v0
//if(mUser.getText().toString.equals("user") == true)
if-eqz v0, :cond_0
5.重新打包並簽名apk(相關工具的使用,查看《安全和逆向》系列博客相關文章),安裝後驗證如下圖,成功“繞過”用戶名和密碼驗證; Android Studio中Opencv的開發環境搭建過程
Android Studio中Opencv的開發環境搭建過程
目錄Opencv的開發環境搭建過程...一、下載並安裝jdk環境...二、下載並安裝Android Studio.三、下載Android SDK.四、下載ndk.五、下載
 Android RecyclerView完全解析
Android RecyclerView完全解析
有段時間沒寫博客了,可能寫博客的時間都用去把妹了吧。說到把妹,偶爾也會在無意間了解一些把妹的技巧,比如雲擒故縱啊什麼的。可能這些技巧前期會有一定的作用,可能會讓妹子對你產
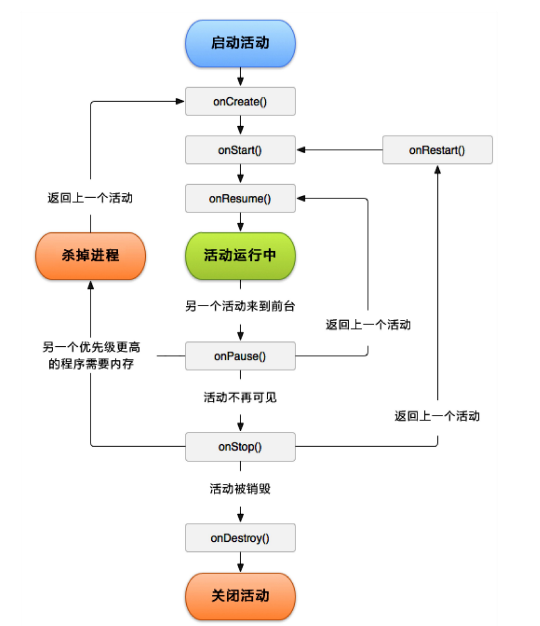 Android四大組件之Activity
Android四大組件之Activity
?Activity?BroadcastReceiver 廣播接收者?Service 服務?ContentProvider 內容提供者Activity的繼承關系public
 Android實戰教程第四十篇之Chronometer實現倒計時
Android實戰教程第四十篇之Chronometer實現倒計時
Android提供了實現按照秒計時的API,今天就是用這個API實現簡單的倒計時。來個布局:<?xml version=1.0 encoding=utf-8